That many ask about how to install wi-fi, no one I know how to add the installation of wi-fi emachine drivers here.
* If you use a laptop
/ notebook, make sure the device is the internal wi-fi has build-in (attached) in your laptop.
* If no, buy the external later installed on the USB port
* Remember the device wi-fi is different from the LAN Card, Modem Card, Ethernet Adapter, Bluetooth. Wi-fi devices are usually accompanied by the category to its wi-fi a / b / g. For example here I use wi-fi Device is Realtek RTL8187 Wireless 802.11g 54Mbps USB 2.0 Network Adapter
* If you have wifi installed, insert the CD driver of the wi-fi is.
* Use the default autorun from the driver CD for easy installation of the driver, or directly click the file setup.exe from the driver wi-fi we (in this case there is a folder in the Azure). For example I use my laptop eMachine.
eMachine the wi-fi Driver but if you have Acer Note Book you must intalling acer drivers, dell drivers for Dell Note Book
* In the sidebar menu Optional driver click Azure Wireless Driver, the installation wizard will appear driver installation in progress wi-fi
finished install wifi.
* Click Next until the window appears as follows
finishing wi-fi instalations.
* Click Finish to complete.
* View on the Device Manager (Windows + R, type devmgmt.msc) has been installed to make sure. Of the image visible on the Network Adapter is highlighted, the driver has been successfully installed.
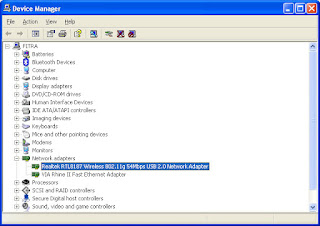
Device manager for wi-fi.
* In Windows Explorer »Control Panel» Network Connections will look like in the picture below (the highlighted section)
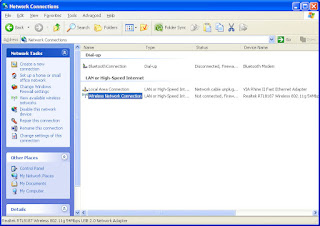
wireless wi-fi connection.
* On the icon tray icon will appear, such as wi-fi in the image below.


